 |
Gray C++ Libraries
0.0.2
A set of C++ libraries for MSVC, GNU on Windows, WinCE, Linux
|
 |
Gray C++ Libraries
0.0.2
A set of C++ libraries for MSVC, GNU on Windows, WinCE, Linux
|
#include <cSSLCommon.h>
Public Member Functions | |
| HRESULT | InitSSL () |
| void | state_SSL_HANDSHAKE_WRAPUP () |
| void | AttachStreams (cStreamInput *pReader, cStreamOutput *pWriter) noexcept |
| virtual void | SetSessionClear () |
| HRESULT | write_SSL_MSG_ALERT (SSL_ALERT_LEVEL_TYPE level, SSL_ALERT_TYPE message) |
| const char * | get_AlpnChosen () const noexcept |
| bool | isStateHandshake () const noexcept |
| HRESULT | Handshake (bool bWait=false) |
| virtual HRESULT | ProcessStreamPacket ()=0 |
| HRESULT | WriteMsgApp (const BYTE *buf, size_t len) |
| void | put_CBCRecordSplitOp (BITOP_TYPE split) |
| X509_Verify_t | get_VerifyResults () const |
| const char * | get_CipherSuiteStr () const |
| const char * | get_VersionStr () const |
| cRefPtr< cX509Crt > | get_PeerCert () const |
| bool | isRenegotiation () const noexcept |
| virtual STREAM_POS_t | GetLength () const override |
| virtual HRESULT | ReadX (OUT void *pData, size_t nDataSize) override |
| virtual size_t | SetSeekSizeMin (size_t nSizeMin=k_FILE_BLOCK_SIZE) override |
| virtual STREAM_SEEKRET_t | Seek (STREAM_OFFSET_t iOffset, SEEK_ORIGIN_TYPE eSeekOrigin=SEEK_Set) override |
| Disambiguate Seek for cStreamBase to cStreamInput for stupid compiler. More... | |
| virtual HRESULT | WriteX (const void *pData, size_t nDataSize) override |
| HRESULT | write_SSL_ALERT_SSL3_CLOSE_NOTIFY () |
| Notify the peer that the connection is being closed. More... | |
| HRESULT | write_SSL_ALERT_SSL3_HANDSHAKE_FAILURE () |
| size_t | build_TLS_EXT_MaxFragmentLength (cSSLMsgHandExt *pExt, SSL_MAX_FRAG_TYPE eMaxFrag) |
| HRESULT | state_SSL_XXX_CERTIFICATE_r () |
| HRESULT | state_SSL_XXX_CERTIFICATE_w () |
| HRESULT | state_SSL_XXX_CHANGE_CIPHER_SPEC_r () |
| HRESULT | state_SSL_XXX_CHANGE_CIPHER_SPEC_w () |
| HRESULT | state_SSL_XXX_FINISHED_r () |
| HRESULT | state_SSL_XXX_FINISHED_w () |
| HRESULT | InitHandshakeParams () |
| HRESULT | BuildKeyExPremasterPSK (SSL_KeyExchange_TYPE key_ex) |
| cKeyWrap * | get_OwnKeyPriv () const noexcept |
| cX509Crt * | get_OwnCert () const noexcept |
 Public Member Functions inherited from Gray::cStream Public Member Functions inherited from Gray::cStream | |
| virtual STREAM_POS_t | GetPosition () const override |
| void | SeekToBegin () |
| STREAM_POS_t | SeekToEnd () |
 Public Member Functions inherited from Gray::cStreamInput Public Member Functions inherited from Gray::cStreamInput | |
| cStreamInput () noexcept | |
| virtual | ~cStreamInput () |
| HRESULT | ReadAll (OUT cHeapBlock &block, size_t nSizeExtra=0) |
| virtual HRESULT | ReadStringLine (OUT char *pszBuffer, StrLen_t iSizeMax) |
| virtual HRESULT | ReadStringLine (OUT wchar_t *pszBuffer, StrLen_t iSizeMax) |
| HRESULT | ReadT (OUT void *pVal, size_t nSize) |
| template<typename TYPE > | |
| HRESULT | ReadT (OUT TYPE &val) |
| template<typename TYPE > | |
| HRESULT | ReadTN (OUT TYPE &val) |
| HRESULT | ReadSize (OUT size_t &nSize) |
| template<typename TYPE > | |
| HRESULT | ReadSizeT (OUT TYPE &n) |
| HRESULT | ReadHashCode (OUT UINT32 &nHashCode) |
| HRESULT | ReadHashCode (OUT UINT64 &nHashCode) |
| HRESULT | ReadN (OUT BYTE *pBuffer, size_t nSizeMax) |
| template<typename _CH > | |
| HRESULT | ReadStringN (OUT _CH *pszStr, StrLen_t iSizeMax) |
| virtual HRESULT | ReadPeek (void *pData, size_t nDataSize) |
 Public Member Functions inherited from Gray::cStreamBase Public Member Functions inherited from Gray::cStreamBase | |
| virtual | ~cStreamBase () |
| void | SeekToBegin () |
| STREAM_POS_t | SeekToEnd () |
 Public Member Functions inherited from Gray::cStreamOutput Public Member Functions inherited from Gray::cStreamOutput | |
| cStreamOutput () noexcept | |
| virtual | ~cStreamOutput () |
| HRESULT | WriteT (const void *pVal, size_t nDataSize) |
| template<typename TYPE > | |
| HRESULT | WriteT (TYPE val) |
| HRESULT | WriteSize (size_t nSize) |
| HRESULT | WriteHashCode (HASHCODE_t nHashCode) |
| HRESULT | WriteN (const void *pBuffer, size_t nSize) |
| template<typename _CH > | |
| HRESULT | WriteStringN (const _CH *pszStr) |
| template<typename _CH > | |
| HRESULT | WriteCharRepeat (_CH nChar, int nCount=1) |
| virtual HRESULT | WriteString (const char *pszStr) |
| virtual HRESULT | WriteString (const wchar_t *pszStr) |
| StrLen_t | VPrintf (const char *pszFormat, va_list args) |
| StrLen_t | VPrintf (const wchar_t *pszFormat, va_list args) |
| StrLen_t _cdecl | Printf (const char *pszFormat,...) |
| StrLen_t _cdecl | Printf (const wchar_t *pszFormat,...) |
| HRESULT | WriteStream (cStreamInput &sInp, STREAM_POS_t nSizeMax=k_FILE_BLOCK_SIZE, IStreamProgressCallback *pProgress=nullptr, TIMESYSD_t nTimeout=0) |
| Copy cStreamInput to this stream. More... | |
| virtual HRESULT | FlushX () |
Public Attributes | |
| const cObjectSignature | m_SigCommon |
| All DLL consumers must agree this is the same. sizeof(*this) More... | |
| const bool | m_bThisIsServer |
| true = cSSLServer else cSSLClient More... | |
| const cSSLConfig & | m_Cfg |
| Behavior controls. More... | |
| SSL_VERSION_TYPE | m_nVer |
| Version selected. either 0 (SSL3) or 1 (TLS1.0) More... | |
| cStreamInput * | m_pReader |
| reading operations raw stream More... | |
| cStreamOutput * | m_pWriter |
| writing operations raw stream More... | |
| bool | m_bRenegotiationSupported |
| does peer support legacy or secure renegotiation TLS_EXT_renegotiation_info More... | |
| cSSLHandshake * | m_pHandshake |
| params required only during the handshake SSL_STATE_TYPE(s) More... | |
| cSSLSession * | m_pSessionNegotiate |
| session data in negotiation. Move to m_pHandshake ? More... | |
| cSSLSession * | m_pSessionCur |
| negotiated session data. swapped from m_pSessionNegotiate More... | |
| cSSLSession * | m_pSessionIn |
| current session data (in) from m_pSessionNegotiate More... | |
| cSSLSession * | m_pSessionOut |
| current session data (out) More... | |
| cSSLTransform * | m_pTransformNegotiate |
| transform params in negotiation. Move to m_pHandshake ? More... | |
| cSSLTransform * | m_pTransformCur |
| negotiated transform params. swapped from m_pTransformNegotiate More... | |
| cSSLTransform * | m_pTransformIn |
| current transform params (in) from m_pTransformNegotiate More... | |
| cSSLTransform * | m_pTransformOut |
| current transform params (in) More... | |
| cSSLMsgBuilder | m_in |
| size_t | m_nInReadPos |
| caller ReadX() offset in application data m_in.m_pMsg More... | |
| cSSLMsgBuilder | m_out |
| message contents (out_iv+ivlen) More... | |
| int | m_nEmptyMessages |
| count # of 0-length encrypted messages. Watch for DoS. More... | |
| bool | m_bClientAuth |
| flag for client auth. client optionally supplies a cert if servers asks. More... | |
| X509_Verify_t | m_eVerifyResults |
| verification result for cert. More... | |
| const char * | m_pszAlpnChosen |
| extension RFC 7301 Application Layer Protocol Negotiation. More... | |
| cHeapBlock | m_PSK |
| cHeapBlock | m_PSKIdentity |
| size_t | m_nVerifyDataSize |
| length of verify data stored. <= k_VERIFY_DATA_MAX_LEN More... | |
| BYTE | m_VerifyDataPeer [k_VERIFY_DATA_MAX_LEN] |
| previous handshake verify data More... | |
| BITOP_TYPE | m_nCBCRecordSplitOp |
| flag for record splitting: BITOP_TOGGLE=disabled, BITOP_CLR=todo, BITOP_SET= done More... | |
| cX509KeyCrtPair * | m_pKeyCrtPair |
| my own certificate(s)/key(s) pair. Not freed. (server only) More... | |
| const char * | m_pszPeerCN |
| expected peer CN in case we check this against cert. More... | |
Static Public Attributes | |
| static const int | k_VERIFY_DATA_MAX_LEN = 36 |
| Length of the verify data for secure renegotiation. SSLv3. More... | |
 Static Public Attributes inherited from Gray::cStreamBase Static Public Attributes inherited from Gray::cStreamBase | |
| static const BYTE | k_SIZE_MASK = 0x80 |
| Used for WriteSize() More... | |
| static const size_t | k_FILE_BLOCK_SIZE = (32 * 1024) |
| default arbitrary transfer block size. more than this is NOT more efficient. More... | |
 Static Public Attributes inherited from GrayLib::cSSL Static Public Attributes inherited from GrayLib::cSSL | |
| static const size_t | k_PSK_Size_Max = 32 |
| 256 bits More... | |
| static const size_t | k_MAC_Size_Max = 48 |
| 16 to 48. SHA-384 used for HMAC. like k_HashSizeMax More... | |
| static const size_t | k_Number_Size_Max = 1024 |
| Max reasonable size of a big number used for crypt purposes. 8k bits. like cBigInteger::k_SIZE_MAX. More... | |
| static const size_t | k_Content_Size_Max = 16384 |
| Size of content. >= k_MaxFragLens[MAX]. More... | |
| static const WORD | k_MaxFragLens [SSL_MAX_FRAG_LEN_QTY] |
Protected Member Functions | |
| cSSLCommon (bool bEndpointIsServer, const cSSLConfig &rOpts) noexcept | |
| virtual | ~cSSLCommon () |
| HRESULT | ReturnError (HRESULT hRes, const char *pszMsg) const |
| SSL_STATE_TYPE | get_State () const noexcept |
| void | put_State (SSL_STATE_TYPE e) noexcept |
| void | IncState1 (SSL_STATE_TYPE e) |
| HRESULT | WriteFlush (bool bWait=false) |
| HRESULT | WriteMsg (SSL_MSG_TYPE eMsg, size_t nContLength) |
| HRESULT | ReadFill (size_t nSizeExpect) |
| HRESULT | ReadCheckHandshake () |
| HRESULT | ReadMessage () |
| HRESULT | ReadProcessCompleteMsg () |
| HRESULT | PrepareKeys () |
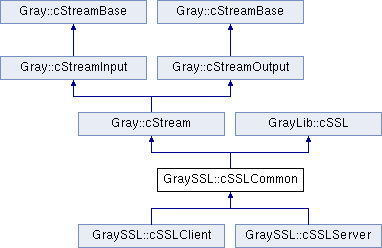
Base for cSSLServer and/or cSSLClient
|
protectednoexcept |
< previous handshake verify data
|
protectedvirtual |
|
inlinenoexcept |
Set the underlying BIO read and write callbacks
| size_t GraySSL::cSSLCommon::build_TLS_EXT_MaxFragmentLength | ( | cSSLMsgHandExt * | pExt, |
| SSL_MAX_FRAG_TYPE | eMaxFrag | ||
| ) |
| HRESULT GraySSL::cSSLCommon::BuildKeyExPremasterPSK | ( | SSL_KeyExchange_TYPE | key_ex | ) |
|
inlinenoexcept |
Get the name of the negotiated Application Layer Protocol. This function should be called after the handshake is completed.
| const char * GraySSL::cSSLCommon::get_CipherSuiteStr | ( | ) | const |
Return the name of the current ciphersuite
|
inlinenoexcept |
|
inlinenoexcept |
|
inlineprotectednoexcept |
| X509_Verify_t GraySSL::cSSLCommon::get_VerifyResults | ( | ) | const |
Get the result of the certificate verification
| const char * GraySSL::cSSLCommon::get_VersionStr | ( | ) | const |
Return the current SSL version (SSLv3/TLSv1/etc)
|
overridevirtual |
Return the number of data bytes available to read
SSL get accessors. m_nInReadPos
Reimplemented from Gray::cStream.
| HRESULT GraySSL::cSSLCommon::Handshake | ( | bool | bWait = false | ) |
Perform the SSL handshake as a single blocking operation. First thing on new connection.
|
inlineprotected |
| HRESULT GraySSL::cSSLCommon::InitHandshakeParams | ( | ) |
| HRESULT GraySSL::cSSLCommon::InitSSL | ( | ) |
Initialize an SSL context (An individual SSL context is not thread - safe)
|
inlinenoexcept |
|
inlinenoexcept |
Are we still in the handshake phase?
|
protected |
|
pure virtual |
Perform a single step of the SSL handshake
Implemented in GraySSL::cSSLServer, and GraySSL::cSSLClient.
| void GraySSL::cSSLCommon::put_CBCRecordSplitOp | ( | BITOP_TYPE | split | ) |
Enable / Disable 1/n-1 record splitting (Default: enable)
|
inlineprotectednoexcept |
|
protected |
|
protected |
|
protected |
Fill m_in For handshake or application data mode message. Does not work for v2 Hello message.
|
protected |
I finished processing the m_in message and can get a new one. (unless it has another handshake message appended) processed just 1 handshake sub packet at a time.
|
overridevirtual |
Read at most 'len' application data bytes
Receive application data decrypted from the SSL layer
Reimplemented from Gray::cStreamInput.
|
overridevirtual |
Disambiguate Seek for cStreamBase to cStreamInput for stupid compiler.
Effect the m_in buffer.
Reimplemented from Gray::cStream.
|
overridevirtual |
Lock a transaction for the stream. I want to Seek() back.
Reimplemented from Gray::cStreamInput.
|
virtual |
Reset an already initialized SSL context for re-use while retaining application-set variables, function pointers and data.
Reimplemented in GraySSL::cSSLClient.
| void GraySSL::cSSLCommon::state_SSL_HANDSHAKE_WRAPUP | ( | ) |
| HRESULT GraySSL::cSSLCommon::state_SSL_XXX_CERTIFICATE_r | ( | ) |
SSL_SERVER_CERTIFICATE (For client) | SSL_CLIENT_CERTIFICATE (for server)
<== ( Certificate/Alert ) ClientKeyExchange ( CertificateVerify ) ChangeCipherSpec Finished
| HRESULT GraySSL::cSSLCommon::state_SSL_XXX_CERTIFICATE_w | ( | ) |
SSL_SERVER_CERTIFICATE (for server) | SSL_CLIENT_CERTIFICATE (For client) Send my public cert.
| HRESULT GraySSL::cSSLCommon::state_SSL_XXX_CHANGE_CIPHER_SPEC_r | ( | ) |
SSL_CLIENT_CHANGE_CIPHER_SPEC (for server) or SSL_SERVER_CHANGE_CIPHER_SPEC (for client) read
| HRESULT GraySSL::cSSLCommon::state_SSL_XXX_CHANGE_CIPHER_SPEC_w | ( | ) |
SSL_CLIENT_CHANGE_CIPHER_SPEC (for client) or SSL_SERVER_CHANGE_CIPHER_SPEC (for server) write
| HRESULT GraySSL::cSSLCommon::state_SSL_XXX_FINISHED_r | ( | ) |
SSL_SERVER_FINISHED (for client) or SSL_CLIENT_FINISHED (for server)
| HRESULT GraySSL::cSSLCommon::state_SSL_XXX_FINISHED_w | ( | ) |
SSL_CLIENT_FINISHED (For client) or SSL_SERVER_FINISHED (for server)
| HRESULT GraySSL::cSSLCommon::write_SSL_ALERT_SSL3_CLOSE_NOTIFY | ( | ) |
Notify the peer that the connection is being closed.
| HRESULT GraySSL::cSSLCommon::write_SSL_ALERT_SSL3_HANDSHAKE_FAILURE | ( | ) |
| HRESULT GraySSL::cSSLCommon::write_SSL_MSG_ALERT | ( | SSL_ALERT_LEVEL_TYPE | level, |
| SSL_ALERT_TYPE | message | ||
| ) |
Send an alert message
|
protected |
|
protected |
Flush m_out Record
| HRESULT GraySSL::cSSLCommon::WriteMsgApp | ( | const BYTE * | buf, |
| size_t | len | ||
| ) |
Send application data to be encrypted by the SSL layer, taking care of max fragment length and buffer size. Maybe Send Partial.
|
overridevirtual |
Write exactly 'len' application data bytes
Reimplemented from Gray::cStreamOutput.
|
static |
Length of the verify data for secure renegotiation. SSLv3.
| bool GraySSL::cSSLCommon::m_bClientAuth |
flag for client auth. client optionally supplies a cert if servers asks.
| bool GraySSL::cSSLCommon::m_bRenegotiationSupported |
does peer support legacy or secure renegotiation TLS_EXT_renegotiation_info
| const bool GraySSL::cSSLCommon::m_bThisIsServer |
true = cSSLServer else cSSLClient
| const cSSLConfig& GraySSL::cSSLCommon::m_Cfg |
Behavior controls.
| X509_Verify_t GraySSL::cSSLCommon::m_eVerifyResults |
verification result for cert.
| cSSLMsgBuilder GraySSL::cSSLCommon::m_in |
| BITOP_TYPE GraySSL::cSSLCommon::m_nCBCRecordSplitOp |
flag for record splitting: BITOP_TOGGLE=disabled, BITOP_CLR=todo, BITOP_SET= done
| int GraySSL::cSSLCommon::m_nEmptyMessages |
count # of 0-length encrypted messages. Watch for DoS.
| size_t GraySSL::cSSLCommon::m_nInReadPos |
caller ReadX() offset in application data m_in.m_pMsg
| SSL_VERSION_TYPE GraySSL::cSSLCommon::m_nVer |
Version selected. either 0 (SSL3) or 1 (TLS1.0)
| size_t GraySSL::cSSLCommon::m_nVerifyDataSize |
length of verify data stored. <= k_VERIFY_DATA_MAX_LEN
| cSSLMsgBuilder GraySSL::cSSLCommon::m_out |
message contents (out_iv+ivlen)
| cSSLHandshake* GraySSL::cSSLCommon::m_pHandshake |
params required only during the handshake SSL_STATE_TYPE(s)
| cX509KeyCrtPair* GraySSL::cSSLCommon::m_pKeyCrtPair |
my own certificate(s)/key(s) pair. Not freed. (server only)
| cStreamInput* GraySSL::cSSLCommon::m_pReader |
reading operations raw stream
| cSSLSession* GraySSL::cSSLCommon::m_pSessionCur |
negotiated session data. swapped from m_pSessionNegotiate
| cSSLSession* GraySSL::cSSLCommon::m_pSessionIn |
current session data (in) from m_pSessionNegotiate
| cSSLSession* GraySSL::cSSLCommon::m_pSessionNegotiate |
session data in negotiation. Move to m_pHandshake ?
| cSSLSession* GraySSL::cSSLCommon::m_pSessionOut |
current session data (out)
| cHeapBlock GraySSL::cSSLCommon::m_PSK |
| cHeapBlock GraySSL::cSSLCommon::m_PSKIdentity |
| const char* GraySSL::cSSLCommon::m_pszAlpnChosen |
extension RFC 7301 Application Layer Protocol Negotiation.
negotiated protocol from m_ppAlpnList. or nullptr.
| const char* GraySSL::cSSLCommon::m_pszPeerCN |
expected peer CN in case we check this against cert.
| cSSLTransform* GraySSL::cSSLCommon::m_pTransformCur |
negotiated transform params. swapped from m_pTransformNegotiate
| cSSLTransform* GraySSL::cSSLCommon::m_pTransformIn |
current transform params (in) from m_pTransformNegotiate
| cSSLTransform* GraySSL::cSSLCommon::m_pTransformNegotiate |
transform params in negotiation. Move to m_pHandshake ?
| cSSLTransform* GraySSL::cSSLCommon::m_pTransformOut |
current transform params (in)
| cStreamOutput* GraySSL::cSSLCommon::m_pWriter |
writing operations raw stream
| const cObjectSignature GraySSL::cSSLCommon::m_SigCommon |
All DLL consumers must agree this is the same. sizeof(*this)
| BYTE GraySSL::cSSLCommon::m_VerifyDataPeer[k_VERIFY_DATA_MAX_LEN] |
previous handshake verify data